Some digital documents are simply too important to leave unprotected. No matter what you do—teach, write, or run a business—safeguarding your work has never been more critical with the rapid increase in cyber threats. These threats aren’t just aimed at big corporations; smaller teams, independent creators, and educators are increasingly being targeted, often because their security measures are easier to bypass. Reports show that 43% of cyberattacks now target small businesses with less than 250 employees.
From data breaches and file leaks to unauthorized sharing and piracy, unsecured documents can cause serious harm. That’s why understanding document security is so important. So in this article, we’ll break down what it is, why it matters, and how you can protect your digital content without getting overwhelmed by technicalities.

What Is Document Security?
Document security is all about keeping your digital files safe from prying eyes, theft, or unwanted changes. It helps make sure that only the right people can open, edit, or share your content. This applies whether it’s saved on your device, stored in the cloud, or sent across different platforms.
At its core, document security is about control. It helps you answer key questions like:
- Who can open this file?
- Can they edit, share, copy, or print it?
- Is the content protected if the file is forwarded or leaked?
- Can I track who accessed or modified it?
Importance of Document Security
Whether you’re running a small business, publishing your own book, or sharing educational materials, your digital documents are valuable. Without proper security, they can be copied, altered, or leaked in a matter of seconds.
Here’s why document security should be a priority:
- Protect your hard work: You’ve spent time creating original content. Securing your documents helps ensure your ideas aren’t stolen, plagiarized, or shared without your consent.
- Maintain privacy and trust: Clients, learners, and partners trust you with sensitive information. Having a strong security system on your digital documents helps you protect their data and keep that trust intact.
- Avoid financial and legal risks: A single leak or data breach can lead to lawsuits, fines, or loss of income, especially if personal or confidential data is involved.
- Stay in control: You can stay in control of your content by using tools that limit access, manage sharing, and monitor who opens or interacts with your files.
- Comply with regulations: Depending on your field, you might be legally required to protect documents (e.g., GDPR and FERPA).
- Prevent data corruption: Good document security can also help prevent your files from getting corrupted by viruses, malware, or faulty storage.

Who Can Benefit from Digital Document Security
Anyone who handles valuable or sensitive information can benefit from having strong security measures in place. It can help protect your work and your reputation, and offer you some peace of mind.
Here are just a few examples of the wide range of people and organizations that could benefit from document security:
- Small business owners securing contracts, invoices, and client data
- Authors protecting manuscripts, publishing rights, and private notes
- Educators and trainers managing course materials, student records, and exam content
- Freelancers and consultants sharing proposals, strategies, or work-in-progress files
- HR and admin professionals safeguarding employee information or internal reports
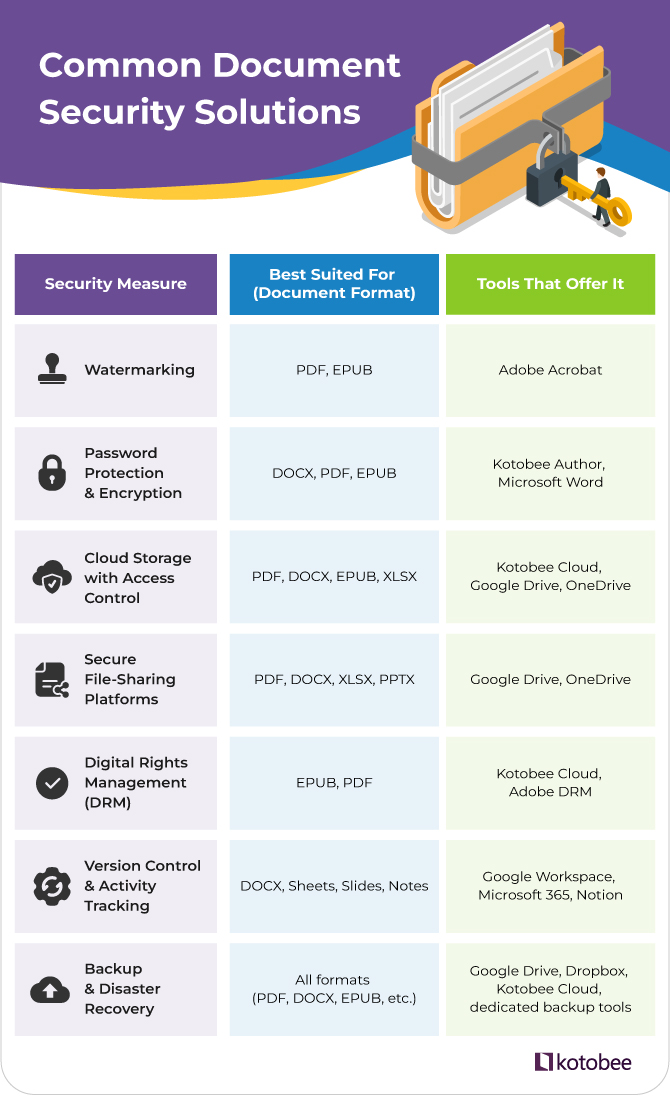
Common Document Security Solutions
Different organizations and individuals use different measures to protect their documents, depending on the level of sensitivity involved. Often, several methods are combined to create stronger, multi-layered security. Many of these tools are already built into the software and services you use every day.
Here are some of the most commonly used document security solutions:
- Watermarking: Watermarks, whether visible or hidden, discourage unauthorized sharing and can help trace leaks back to specific users by embedding identifying information—such as a unique ID—directly into the document. An easy way to add such watermarks is through Adobe Acrobat.
- Password protection and encryption: Setting strong passwords is a basic first step. Encryption, on the other hand, locks your document’s content so that only people with permission can read it, even if someone else gets hold of the file. This can be done simply by using tools like Kotobee Author or Microsoft Word.
- Cloud storage with strong access control: Cloud services offer secure file storage, especially when you use features like two-factor authentication, permission settings, and customizable sharing controls. Platforms like Kotobee Cloud also provide controlled access to digital publications, including DRM and user authentication.
- Secure file-sharing platforms: Instead of sending documents through unsecured email attachments, platforms like Google Drive and OneDrive offer safer ways to share files. Some of them also allow you to set permissions, restrict downloads, and track who accesses your documents.
- Digital Rights Management (DRM): DRM tools allow you to control how your documents are accessed, shared, or printed. You can also set expiration dates or revoke access if needed.
- Version control and activity tracking: Keeping track of changes and monitoring how documents are accessed are both essential for secure collaboration. Tools like Google Workspace, Microsoft 365, and Notion offer built-in version history and detailed user activity logs to support safe, efficient teamwork.
- Backup and disaster recovery: Document security also includes being ready for accidents or cyberattacks. Regular backups and a disaster recovery plan can protect your work from loss or damage.
💡Pro tip: For the best protection, combine several solutions. Relying on just one layer of security can leave your documents vulnerable.
Document Security in Action: Practical Tips and Best Practices
Even the strongest security measures can fall short if they aren’t applied thoughtfully. Good document security comes from consistent, everyday habits that help you minimize risks, safeguard your sensitive content, and stay in control of your files at all times.
Here are some smart ways to put document security into action:
- Limit who can see your documents: Give access only to people who truly need it. For example, if you’re collaborating on a draft, send it directly to your team members rather than generating a public link that anyone can open.
- Use secure networks: Avoid working on sensitive files when connected to public Wi-Fi. Always use trusted, secure internet connections or use a VPN for extra safety.
- Keep devices protected: A strong password, a reliable antivirus program, and regular software updates can go a long way toward keeping your documents safe. You should also enable screen locks and auto-lock features on your devices to prevent unauthorized access.
- Remove old files: Don’t leave sensitive documents sitting on shared computers or unsecured drives. Archive what you need and securely delete what you don’t.
- Track access regularly: If your tools allow it, check who has viewed or edited your files. If you see unfamiliar access, revoke permissions and change your sharing settings.
- Prepare for the unexpected: Always have backup copies of important documents stored safely. If something goes wrong, you won’t lose your data.
How to Secure Your Documents with Kotobee
If you’re looking for an easy and trustworthy way to protect your documents, Kotobee offers several built-in options that can help. Whether you’re creating educational material, sharing company training resources, or publishing ebooks, you can apply different levels of security depending on your needs.
Some of the ways Kotobee supports document security include:
- Password protection and user restrictions to control who can open and read your content.
💡Use case: A university instructor creates an interactive textbook in EPUB format using Kotobee Author and restricts access to only enrolled students. Each student must log in with their email and password to view the book.
- Digital Rights Management (DRM) features to limit copying, printing, and sharing without permission
💡Use case: A corporate training department distributes a confidential product manual. To prevent leaks, they enable DRM to block users from copying or printing any part of the document or sharing it with competitors.
- Secure cloud hosting with encrypted access to keep your documents safe online
💡Use case: A self-published author uploads their ebook to Kotobee Cloud. The file is stored securely with encryption, and only authorized users with the right credentials can access it. This helps prevent piracy and unauthorized distribution.
- Two-Factor Authentication (2FA) to secure access by requiring both a serial number and a one-time password (OTP) sent to your email
💡Use case: An online learning platform offers premium courses in ebook format. To prevent unauthorized logins, Kotobee’s 2FA sends a one-time password to the user’s registered email, adding a second layer of security in addition to the standard serial key.
- Access duration control to set a limited time for how long a user can access your documents, which is perfect for temporary or subscription-based access
💡Use case: A training provider offers 30-day access to a certification guide. Using Kotobee, they set a time limit so the ebook becomes inaccessible after the allotted period. This can also be ideal for trial runs, rentals, or time-sensitive learning.
- Device limitation options to restrict the number of devices each user can use to open your documents, helping prevent account sharing.
💡Use case: A publisher sells an ebook to individual readers and limits access to two devices per user. This prevents account sharing while still allowing flexibility for users to read on both their tablet and laptop.
How Organizations Use Kotobee to Safeguard Their Digital Content
Digital content protection is more than just a nice-to-have option. For many organizations, it’s a key part of their strategy to deliver content with confidence, maintain ownership, and ensure only the right people have access. To support these goals, Kotobee’s security tools have helped educators, trainers, and institutions around the world protect their work and maintain control. Here are a few real examples of that success in action:
- Australia’s Leading RePL Trainer: UAVAIR, a recognized name in drone training, needed a way to prevent their training manuals from being shared without authorization. By using Kotobee’s DRM features and access controls, they secured their learning materials while keeping the experience smooth for students.
- TaF.tc: Singapore’s Textile and Fashion Training Centre (TaF.tc) wanted to secure their course content and move away from printed materials. With Kotobee, they were able to deliver their training digitally using login protection, which strengthened content privacy.
- Virginia Tech: Professors at Virginia Tech created a multimedia textbook on 5G technology and needed a secure way to share it with students. Kotobee allowed them to publish their work with full access management and content tracking, ensuring their materials stayed protected and current.
Final Thoughts
Securing your documents doesn’t have to be complicated. With the right tools and a few smart practices, you can protect your valuable content and ensure it stays in the right hands. It doesn’t matter whether you’re an author, educator, or small business owner; taking steps to safeguard your work can help you maintain control and avoid any unnecessary risks.
.
Read More
What Is a Webbook and How to Create One


